How to Create a Comprehensive Zero Trust Strategy
Most experts agree that taking a zero-trust approach to cybersecurity is critical to fighting cybercrime. The concepts behind the zero-trust security model are straightforward, addressing the risk associated with unchecked access. Instead of assuming anyone or anything that has gained access to the network can be trusted, zero trust assumes the opposite. Nothing can be trusted anywhere, whether outside or inside the network perimeter.
The traditional perimeter-based network security model no longer works for today’s highly complex networks because it grants excessive implicit trust. But the zero-trust security model doesn’t base trust on network location. Instead, it starts with a default deny posture for everything and evaluates trust on a per-transaction basis. Whenever a user or device requests access to a resource, it must be verified based on identity and context, such as time, date, and geolocation. After verification, access is given based on the principle of least privilege. If a user requests access to a particular application and is verified, access to that application is the only access that is granted. Another key tenet of zero trust is that trust must be continually reevaluated. If important attributes change, the verification may be revoked and access removed.
Network Architectures Change
What Is a Zero-Trust Strategy?
With a comprehensive zero-trust strategy, organizations can implement robust data protection across on-premises, hybrid, and m
ulti-cloud environments. According to a Fortinet survey, 84% of companies have a zero-trust strategy in place. Those organizations planning their zero-trust strategies should consider using a framework such as the Zero Trust Maturity Model from the Cybersecurity and Infrastructure Security Agency (CISA) for guiding principles. These principles are the foundation of any zero-trust strategy as they help protect digital assets and mitigate breaches.
In the United States, the increased interest in implementing zero-trust principles is partly because of the 2021 White House Executive Order (EO) 14028, “Improving the Nation’s Cybersecurity,” which initiated a governmentwide effort to ensure that baseline security practices are in place and to migrate the federal government to a zero-trust architecture. Following the EO, the Office of Management and Budget (OMB) published the Directive M-22-09 Federal Zero Trust Strategy in January 2022. This directive pushes agencies to adopt zero-trust cybersecurity principles and adjust their networks to meet specific security standards by the end of fiscal year 2024, referencing both the Department of Defense Zero Trust Reference Architecture and the CISA Zero Trust Maturity Model. The adoption of zero-trust strategies in the federal government has had a ripple effect on private-sector businesses with government contracts as well.
Zero-trust concepts have also become more important in today’s work-from-anywhere (WFA) world. Organizations are struggling to deal with ever-increasing threats from ransomware, phishing, botnets, and other criminal activity. With users, devices, and applications all in multiple locations, traditional perimeter-based solutions aren’t an effective or scalable way to secure access to critical resources anymore. The implementation of zero-trust security principles offers a practical approach that can help enterprises or other businesses manage remote staff while ensuring proper security protocols are in place.
Implementing zero-trust principles doesn’t necessarily require completely starting over with your network. Designing a zero-trust strategy is about pairing the right framework with the right tools. Often, the biggest change is in mindset. Organizations need to make a commitment to changing how access is granted and how security is maintained throughout the company. The second version of the CISA Zero Trust Maturity Model, released in April 2022, lists five pillars, which should be part of any zero-trust security strategy:
- Identity
- Devices
- Networks
- Applications and workloads
- Data
Know and Control Everyone and Everything on the Network
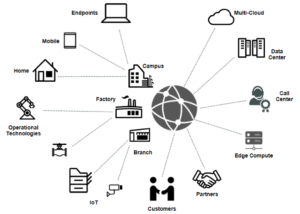
Setting Up a Comprehensive Zero-Trust Strategy
Setting up a zero-trust strategy will be a different journey for every organization because every company’s IT environment and current security posture are unique. Zero-trust access (ZTA) applies zero-trust principles to users and their devices and also to non-user-associated devices, such as Internet-of-Things (IoT) devices. ZTA is about knowing and controlling both who and what is on your network.
Securing identity
The first step in developing a zero-trust strategy is to decide who in your workforce is allowed to do what. Zero trust should start with identity: You need to determine who gets access to which resources based on specific requirements. People should be able to access the resources required to do their jobs and nothing more. Role-based access control is a critical component of access management. Only by knowing definitively who a user is can the appropriate level of access be granted based on their role. Is the user an employee, a guest, or a contractor? What is their role, and what network access rights does that role entitle them to?
Identifying and authenticating users prior to granting access is a critical security requirement. Identity and access management (IAM) solutions define user access to resources as precisely as possible so they can prevent risks arising from unauthorized or excess access. A robust IAM program incorporates, at minimum, the following advanced security measures:
- Multi-factor authentication: a combination of something a person knows (password), has (token or device), and is (biometric)
- Role-based access control (RBAC): tying access to a user’s job function
- Attribute-based access control (ABAC): tying user access to additional user attributes like geographic region, device, or time of day
Often, organizations use Single Sign-on (SSO) to make these processes faster and easier for the end-users.
Securing devices and networks
Next, you will need to make sure the devices that people are using are properly secured. Establishing ZTA involves pervasive application access controls, powerful network access control technologies, and strong authentication capabilities for both user-associated devices and non-user-associated devices. User-associated devices, such as laptops or mobile phones, have some type of agent that assesses the state of the device. Non-user-associated devices include the growing number of “headless” network-connected devices that may include IoT devices, such as printers, heating, and ventilation devices, or door access systems. Because these devices do not have a username or password to identify themselves and a role, organizations must use network access control (NAC) solutions to discover and control access. By setting up NAC policies, you can apply the zero-trust principles of least access to these IoT devices, granting sufficient network access to perform their tasks and nothing more. As devices connect and disconnect from networks, organizations need:
- Network access control: to automatically identify, profile, and scan devices before granting access
- Next-generation firewalls (NGFWs): to microsegment networks and group similar IoT devices together
- Endpoint detection and response (EDR): to detect and defuse potential threats in real-time
Securing application access
One aspect of ZTA that focuses on controlling access to applications is zero-trust network access (ZTNA). Zero-trust network access extends the principles of ZTA to verify users and devices before every application session to confirm that they conform to the organization’s policy to access that application. It also supports multi-factor authentication to maintain the highest degree of verification.
By using the zero-trust model for application access, organizations can rely less on traditional virtual private network (VPN) tunnels to hide traffic as it travels across the internet. Because a VPN often provides unrestricted access to the network, it can allow compromised users or malware to move laterally across the network, seeking resources to exploit. With a VPN, the assumption is that anyone or anything that passes network perimeter controls can be trusted. But ZTNA takes the opposite approach: No user or device can be trusted to access anything until proven otherwise. Unlike a VPN, ZTNA extends the zero-trust model beyond the network and reduces the attack surface by hiding applications from the internet.
Because of the prevalence of remote working, ZTNA has received more attention lately. It’s a way of controlling access to applications regardless of where the user or the application resides. However, ZTNA should apply to all users everywhere. In today’s WFA world, users may be on a corporate network, working from home, or elsewhere. And the application may reside in a corporate data center, in a private cloud, or on the public internet. Zero-trust network access applies security policies equally, whether users are on or off the network. So, an organization has the same protections, no matter where a user is connecting from.
To ensure that users and the devices connecting to their networks comply with security policies prior to granting them network and resource access, organizations may use one or more solutions:
- Zero-trust network access: to verify users and devices before every application session
- Virtual private networks: to secure access from the devices to corporate networks
- Secure access service edge (SASE): to converge networking and security by combining integrated SD-WAN with network security solutions
Going Beyond Basic Controls
Although a zero-trust strategy requires controls across a series of defined pillars, the process requires continuous iteration. For example, in dynamic cloud environments, a company’s security posture continuously evolves, which can render some controls ineffective. In modern, interconnected environments, manually managing controls across all of the key pillars can be overwhelming and unsustainable. As an organization’s zero-trust strategy matures, it needs to move beyond the basic controls and consider technologies that enable:
- Visibility and analytics: centralized visibility and interoperability across all pillars
- Automation and orchestration: continuous real-time identity and security validation and enforcement that uses machine learning (ML) to enforce policies
- Governance: cross-pillar coordination with dynamic policies and automated attribute assignation to assets and resources
To create an effective zero-trust strategy, consistent protocols and policies must be implemented across the entire network. Most companies have taken a hybrid approach to their networks, yet many zero-trust solution providers are developing cloud-only solutions. Because the rules must be consistent, most organizations need zero-trust security tools that aren’t cloud-only. Organizations with hybrid networks need to use the same zero-trust security tools with remote workers that they use on the physical campus.
Controlling Access to Hybrid-Cloud Architectures
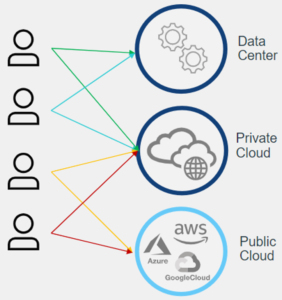
It’s critical to make sure your zero-trust security strategy provides the same protocols, no matter where the user or the application is located. Many companies include multiple cloud platforms and applications as part of their network, each with different capabilities, tools, and functions. But each of these cloud environments could become an independent silo from a security standpoint, leading to a fragmented network security infrastructure. To avoid this issue, organizations should have a common security overlay across all of their data centers and clouds. This abstraction layer above the individual tools provides visibility and control across all of the clouds and the ability to establish security regardless of application location.
Potential Challenges in Implementing a Zero-Trust Strategy
Successful zero-trust implementation is crucial to ensuring your strategy works and that your organization is protected. However, implementing zero trust is a journey, and like any journey, roadblocks may appear, especially at the beginning. Organizations may encounter challenges related to:
- Lack of skills and budget: The demand for staff with cybersecurity experience continues to outpace the number of people to fill jobs. Combined with limited budgets, many organizations struggle to find, hire, and retain the staff they need to implement an effective zero-trust strategy.
- Disconnected tools: A successful zero-trust strategy requires visibility across all pillars. Many companies invested in tools that respond to individual pillars, like using an IAM system and anti-malware software. If these tools are incompatible, the organization is unable to connect the user’s access to the device’s security posture.
- Resistance to change: In some cases, the company faces internal resistance from both IT stakeholders and end-users. IT stakeholders often maintain that traditional strategies, like deploying VPNs, are enough to secure users’ access to networks. Simultaneously, end-users argue that the security controls, like authenticating at the start of each application session, make their jobs more time-consuming or difficult.
Selecting the right technology can be another source of difficulty. As organizations build out their zero-trust initiatives, they must carefully consider their technology investments.
Elements of a Zero-Trust Solution
A robust zero-trust technology stack should provide both visibility and automation to streamline end-user experiences and reduce security team burdens. Organizations should ensure they have these product areas and capabilities.
Identity and access management
A robust IAM technology securely and effectively manages authentication and authorization for all systems and applications by:
- Establishing identity through login, MFA, and certificates, which may evolve to add continuous contextual authentication
- Providing role-based information from an authentication source for use in privileged access
- Establishing and enforcing role-based least access policies
- Providing added security with support for SSO to help improve user compliance and adoption
- Verifying ZTNA connections for devices and users on a per-session basis to individual applications
- Providing privileged access management (PAM) to monitor critical users and their access
Endpoint access control
With end-users connecting from anywhere, organizations need to combine their IAM strategies with endpoint access technologies that discover, monitor, and assess risks to:
- Support secure, encrypted connections across unsafe networks with support for split tunneling and SASE services
- Provide continuous endpoint security telemetry data, including device operating system (OS) and applications, known vulnerabilities, patches, and security status
- Support ZTNA remote access, which simplifies secure connectivity, providing seamless access to applications no matter where the user or the application may be located
Network access control
A NAC layers control on top of the IAM and endpoint access tools by enforcing dynamic policy controls across users on the network. These technologies typically enable an organization to:
- Identify, profile, and scan all devices for vulnerabilities
- Establish and ensure ongoing network control
- Establish and enforce policies that limit network access to only what is needed for that device
- Maintain automated response and network orchestration
Application access control
Once users gain access to the network, an organization needs to ensure that users only access the applications necessary to complete their job functions. As companies look for ZTNA solutions to solve these problems, they should look for ones that:
- Verify users and devices for each application session
- Control user access to applications based on policy
- Enforce application access policy no matter where the user is located, including in the office
- Create a secure, encrypted automatic connection between the user and ZTNA proxy point
- Work with firewalls, VM firewalls, and SASE services
Security operations
With tightly integrated and interoperable technologies across the fundamental ZTA pillars, organizations need a single pane of glass where they can monitor any anomalous activity and then automate responses. When looking to tie all these technologies together for enhanced visibility, companies should consider technologies that:
- Detect threats and enforce security everywhere
- Integrate AI-powered centralized analysis and automated prevention
- Build a context-aware, self-healing network for coordinated protection
How Fortinet Can Help
As the network perimeter continues to dissolve, it is critical that organizations move to implement a zero-trust security strategy. Because so many potential security threats exist both from outside and within the network, it makes sense to treat every user and device that tries to gain access to the network and its applications as a threat. Creating a comprehensive zero-trust security strategy and implementing the necessary security measures doesn’t necessarily require a total network overhaul. Still, it will require time and effort to improve your security posture.
ZTNA Architecture
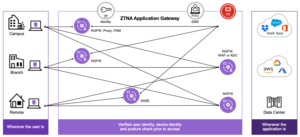
Fortinet offers zero-trust-related solutions that are part of the Fortinet Security Fabric, so organizations can implement key zero-trust security controls and leverage automation to maintain effectiveness. Because Fortinet solutions are tightly integrated through the Security Fabric, customers can layer controls across IAM, endpoints, networks, applications, and data to mitigate security risks.
Fortinet zero-trust solutions continually verify who and what can access networks and applications without negatively impacting user productivity. From IoT to user-owned devices, Fortinet solutions can identify endpoints and enforce security policies, ensuring that IT teams have full visibility into and control over what’s connected to networks.

